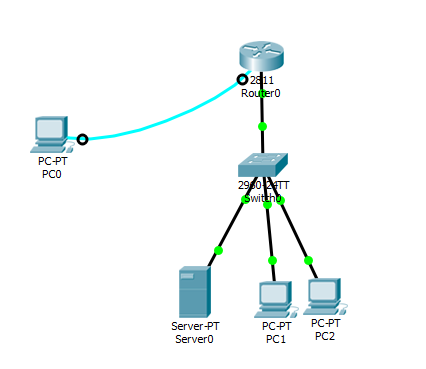
SSH version 2 configuration steps on cisco
The SSH protocol (Secure Shell) is a secure method for remotely logging into other devices. It establishes a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server.SSH is available in two versions –
SSH version 1
SSH v1 (Secure Shell) offers users an encrypted channel for logging into remote devices, ensuring robust host-to-host and user authentication. Moreover, it facilitates secure and encrypted communications over the Internet.
SSH version2
Contrarily, SSH2 stands out as an enhanced and highly secure version of SSH, encompassing the advantageous addition of SFTP. SFTP, similar to FTP but with the added layer of SSH2 encryption, enhances functionality. SSH operates on port 22 and serves as a secure alternative to vulnerable login protocols like Telnet, as well as insecure file transfer methods such as FTP.
To set up SSH, follow these configuration steps:
- Set the router hostname using the “hostname” command.
- Configure the domain name using the “ip domain-name” command.
- Generate public and private keys by executing the “crypto key generate rsa” command.
- Create a user in the local database using the “username…” command.
- Restrict VTY lines to allow only SSH access using the “transport input ssh” command.
Step 1
cisco>enable
cisco#configure terminal
Then press “Y”
cisco(config)#hostname R1
Step 2
R1(config)#ip domain-name techybaniya.com
Step 3
R1(config)#crypto key generate rsa usage-keys label techy modulus 768
Note:- For SSH Version 2, the modulus size must be at least 768 bits.
“The modulus size represents the key size in bits divided by 8. Therefore, a 1024-bit RSA key with OAEP padding can encrypt a maximum of (1024/8) – 42 = 128 – 42 = 86 bytes.”
“On the other hand, a 2048-bit key can encrypt up to (2048/8) – 42 = 256 – 42 = 214 bytes.”
R1(config)#ip ssh authentication-retries 5
R1(config)#ip ssh version 2
R1(config)#ip ssh timeout 120
Step 4
R1(config)#aaa new-model
R1(config)#username cisco Password cisco
Step 5-
R1(config)#line vty 0 4
R1(config)#login local (no need for aaa new-model)
R1(config)#transport input ssh
- If you generate special-usage keys, two pairs of RSA keys will be generated. One pair will be used with any Internet Key Exchange (IKE) policy that specifies RSA signatures as the authentication method, and the other pair will be used with any IKE policy that specifies RSA encrypted keys as the authentication method.
- A CA is used only with IKE policies specifying RSA signatures, not with IKE policies specifying RSA-encrypted nonces. (However, you could specify more than one IKE policy and have RSA signatures specified in one policy and RSA-encrypted nonces in another policy.)
- If you plan to have both types of RSA authentication methods in your IKE policies, you may prefer to generate special-usage keys. With special-usage keys, each key is not unnecessarily exposed. (Without special-usage keys, one key is used for both authentication methods, increasing the exposure of that key.
General-Purpose Keys
When generating general-purpose keys, a single pair of RSA keys will be generated. This pair is utilized with IKE policies that specify either RSA signatures or RSA encrypted keys. Consequently, the general-purpose key pair may be employed more frequently compared to a key pair designed for specific purposes.
Named Key Pairs
When generating a named key pair using the ‘key-label’ argument, it is necessary to specify either the ‘usage-keys’ keyword or the ‘general-keys’ keyword. Named key pairs provide the flexibility of having multiple RSA key pairs, allowing the Cisco IOS software to maintain a distinct key pair for each identity certificate.
“The optimal size for an RSA modulus depends on individual security requirements. A larger modulus ensures higher security but also results in slower RSA operations. When determining the modulus length, it is essential to consider two factors. First, assess your security needs, including the value and duration of the protected data. Second, consider the capabilities of potential adversaries to make an informed decision about the appropriate modulus size.”
Why some cryptographic keys are much smaller than others?
What is SSH in Cisco?
SSH stands for Secure Shell and it is a network protocol that provides secure encrypted communication between two networked devices. In the context of Cisco networking equipment, SSH is used as a secure method for accessing and managing Cisco devices remotely.
How to connect Cisco switch SSH?
To connect to a Cisco switch using SSH, follow these steps:
1. Ensure that your Cisco switch has SSH enabled and configured. You can verify this by checking the switch’s configuration or consulting the network administrator.
2. Open a terminal or SSH client application on your computer. Examples of popular SSH clients include PuTTY (Windows), Terminal (Mac), or OpenSSH (Linux).
3. Obtain the IP address or hostname of the Cisco switch that you want to connect to. 4. This information should be provided by your network administrator or be available in the switch’s configuration.
5. Open your SSH client and enter the IP address or hostname of the Cisco switch in the appropriate field.
6. Specify the SSH port, which is typically port 22 for SSH connections. If the Cisco switch is configured to use a different SSH port, enter that port number instead.
7. Select the SSH protocol for the connection, typically SSH version 2.
8. Click the “Connect” or “Enter” button to initiate the SSH connection.
9. If prompted, enter your username and password. These credentials should be provided by your network administrator. Note that the password may not be displayed on the screen for security reasons.
10. Once authenticated, you should be successfully connected to the Cisco switch using SSH. You will now have access to the switch’s command-line interface (CLI) and can execute commands to configure or manage the switch.
11. Remember to properly exit the SSH session when you are finished by using the appropriate command (e.g., “exit” or “logout”) to ensure a clean disconnection.
Why is SSH used?
SSH (Secure Shell) is used for several reasons, primarily related to security and remote administration:
1. Secure Remote Access: SSH provides a secure method for remotely accessing and managing network devices, servers, and systems. It encrypts the communication between the client and the server, protecting sensitive information such as usernames, passwords, and data transmitted over the network.
2. Authentication and Authorization: SSH employs strong authentication mechanisms to verify the identity of the connecting parties. It supports various authentication methods, including passwords, public key authentication, and certificate-based authentication. This ensures that only authorized users can access the system.
3. Data Encryption: SSH encrypts the data exchanged between the client and the server, making it unreadable to eavesdroppers. This is crucial when transmitting sensitive information, confidential data, or executing commands remotely.
4. Secure File Transfer: In addition to remote shell access, SSH enables secure file transfer between systems using protocols like SCP (Secure Copy) and SFTP (Secure File Transfer Protocol). This allows for secure and reliable file transfers over an insecure network.
5. Tunneling and Port Forwarding: SSH supports tunneling, which allows users to securely access services and resources on a remote network. It can forward specific ports, creating an encrypted channel for accessing services like web servers, databases, or email servers that would otherwise be inaccessible due to network restrictions.
6. Security Compliance: SSH is widely adopted in security-conscious environments and adheres to industry-standard encryption algorithms and protocols. Its use helps organizations meet security compliance requirements and maintain a secure network infrastructure.
7. Overall, SSH is used to establish secure, encrypted connections for remote administration, secure file transfers, and secure access to network services. It plays a vital role in protecting sensitive information, maintaining the integrity of systems, and ensuring secure communication over untrusted networks.
What port uses SSH?
SSH (Secure Shell) typically uses port 22 as the default port for communication. Port 22 is assigned to SSH in the well-known port number range, and it is the standard port used for SSH connections.
Can we define another port number for SSH?
However, it’s worth noting that SSH can be configured to use different port numbers if desired. This can be done for security reasons or to avoid conflicts with other services running on the same system. In such cases, the SSH server would be configured to listen on the specified port, and the SSH client would need to connect to that specific port.
If you are connecting to an SSH server, it is recommended to use port 22 unless instructed otherwise by the server administrator. When using SSH client software, you can usually specify the port number during the connection setup if it is different from the default port.
Keep in mind that firewalls and network security configurations may need to allow incoming and outgoing connections on the designated SSH port to establish successful SSH connections.